Based on the core concept of Quantum Trilogy – a private enclave connected through the Internet to dedicated private servers and using genuine proprietary quantum devices to secure communications – our flagship application allows your personnel and clients to speak in a totally secure and private environment.
Whether you are making calls, sending files, or text messages, Quantum Voice is the ultimate solution for security-sensitive information.
Protected by our patented quantum encryption technology, your communications are always safe.
Our proprietary Quantum Random Number Generator (QRNG), fully integrated between your devices and our back-end servers, dramatically magnify the entropy (*) of our End – to – End encryption.

Quantum Voice is always used in a private enclave which dramatically secures voice communications.
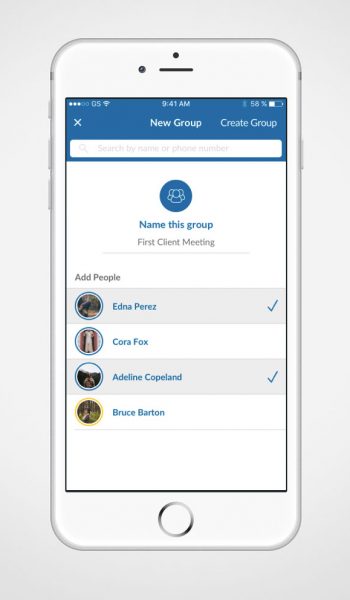
Each external party, such as clients, can only talk to the person that invited them, and by design, cannot speak to any unauthorized user, drastically reducing the possibility of social engineering.
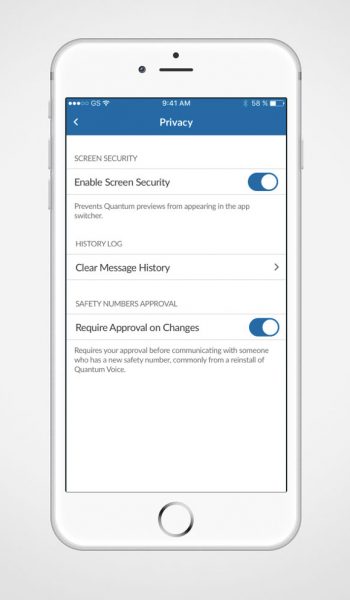
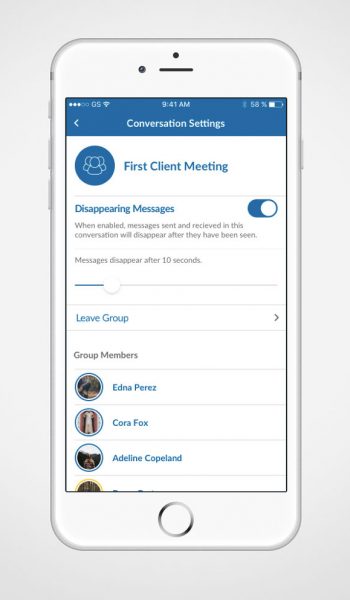
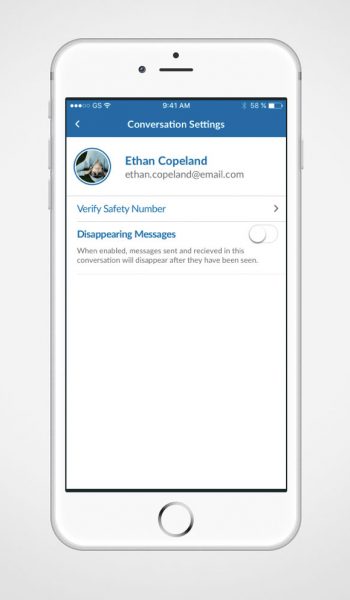
With Quantum Voice, you can select your own message retention policy by choosing how long a message is viewable before it is deleted.
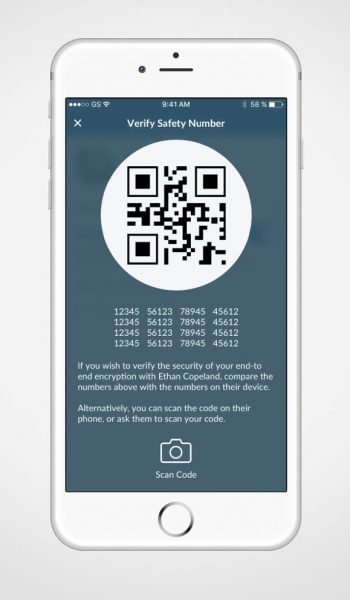
Quantum Voice is resistant to eavesdropping thanks to End – to – End quantum encryption. This means your device encrypts your data to a key which only your recipient has. The data you send may only be decrypted by your intended recipient.
Furthermore, to ensure an unmatched secured voice and messaging communication systems, the Quantum Trilogy Platform integrates an exclusive set of security tools known as Kernel Assurance©, which includes a:
- Version Check
- Software Whitelist
- Hardware Check
All Quantum Voice communications pass through Ethernet, Mobile Data Networks, or Wi-Fi. The data in motion is secured by End-to-End quantum encryption. The Internet Service Provider (ISP) or any potential eavesdropper may only be able to see a connection between your network and our Quantum Trilogy servers. The message cannot even be decrypted by Quantum Trilogy; it can only be decrypted by the intended recipient.
(*) In computing, entropy is the randomness collected by an operating system or application for use in cryptography.